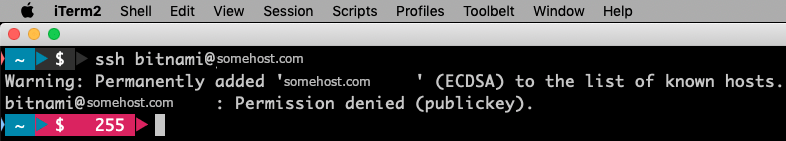
If you use SSH (Secure Shell), you’ve likely encountered the “Permission denied (publickey)” error. This comprehensive guide will help you fix this common issue by properly setting SSH key permissions on your system, whether you’re using Windows or Linux.
Understanding SSH Key Permissions
SSH key permissions are crucial for security. If your key files have incorrect permissions, SSH will refuse to use them, resulting in the “Permission denied (publickey)” error. This is a security feature, not a bug.
Why Permissions Matter
SSH enforces strict permission requirements because:
- Private keys must be kept secure and accessible only to their owner
- Public keys can be shared but should still have appropriate restrictions
- Directory permissions protect against unauthorized access
Prerequisites
Before you begin, ensure you have:
- SSH installed on your system
- An SSH key pair generated (if not, use ssh-keygen)
- Access to your SSH key files
- Administrative privileges (for Windows)
Setting SSH Key Permissions
For Linux/Unix Systems
On Linux and Unix-based systems, your SSH keys are typically located at:
- Private key:
~/.ssh/id_rsa - Public key:
~/.ssh/id_rsa.pub
Set the correct permissions using these commands:
# Set directory permissions
chmod 700 ~/.ssh
# Set private key permissions (read/write for owner only)
chmod 600 ~/.ssh/id_rsa
# Set public key permissions (readable by all, writable by owner)
chmod 644 ~/.ssh/id_rsa.pubFor Windows Systems
On Windows, your SSH keys are typically located at:
%USERPROFILE%\.ssh\id_rsa%USERPROFILE%\.ssh\id_rsa.pub
Set the correct permissions using PowerShell:
- Remove inheritance:
icacls path/to/key/keyfile /inheritance:r- Grant read access to your user:
icacls file /grant:r yourusername:"(R)"Troubleshooting Common Issues
1. Key File Location
- Verify your key files are in the correct location
- Check file names match your SSH configuration
- Ensure the
.sshdirectory exists and has correct permissions
2. File Ownership
- Ensure you own the key files
- Check file ownership with
ls -l(Linux) ordir(Windows) - Fix ownership issues with
chown(Linux) oricacls(Windows)
3. SSH Configuration
- Verify your SSH config file (
~/.ssh/config) is properly configured - Check the key path in your config matches your actual key location
- Ensure the config file has correct permissions (600)
4. Permission Verification
On Linux/Unix:
# Check directory permissions
ls -ld ~/.ssh
# Check key file permissions
ls -l ~/.ssh/id_rsa*On Windows:
# Check file permissions
icacls %USERPROFILE%\.ssh\id_rsaSecurity Best Practices
Keep your private key secure
- Never share your private key
- Use strong passphrases
- Store keys in secure locations
Use appropriate permissions
- 600 for private keys (owner read/write only)
- 644 for public keys (readable by all)
- 700 for .ssh directory (owner access only)
Regular maintenance
- Rotate SSH keys periodically
- Audit key usage
- Remove unused keys
Additional security measures
- Use SSH key passphrases
- Enable SSH agent forwarding when needed
- Monitor SSH access logs
Comments #